Writeup CTF 0x00sec Web - Exercise 1

Writeup CTF 0x00sec Web - Exercise #1
I was excited as I read that there will be bi-monthly CTF exercises on 0x00sec as I wanted to do some CTFs for a long time now.
Challenge
The challenge or exercise was in the web category. Which means that we have to take a look at web-based attacks like SQL Injections, Cross-Site Scripting and others. It is always good to have the OWASP Top 10 in mind.
The challenges description was:
Get the flag! There are multiple ways to achieve your goal :)
And an URL was provided.
Initial Recon
If we open up the URL in a browser, we see a simple login page, where you can enter a username and a password.
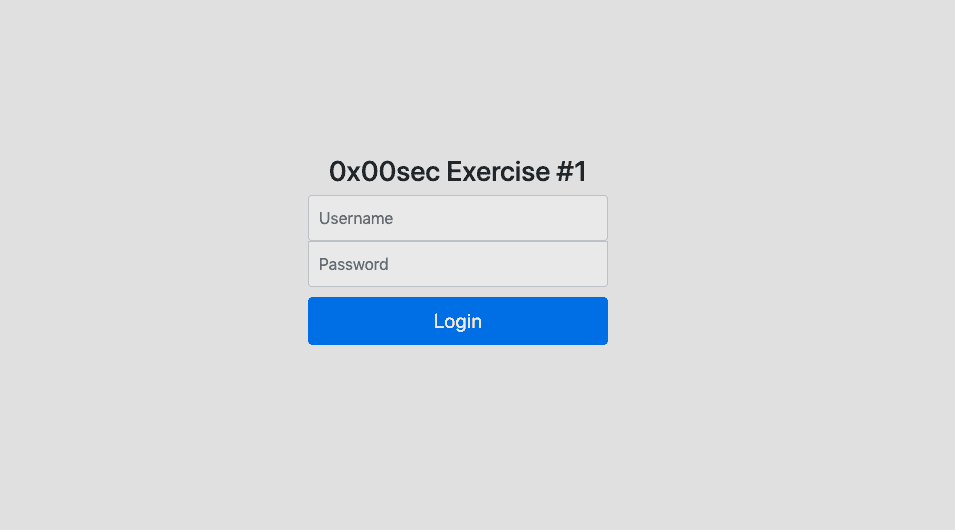
If you see a login field in a CTF, SQL injections may be the first thing that comes to your mind. But it is always good to do some basic recon first.
Because it is just a simple page with a login field and no links to subpages, we are quite limited with the visual recon. But what we can do, is to view the page source. This is something that you should always do because you can find quite interesting information in the page source like:
- Javascript and external javascript files
- Hidden inputs
- Leftover comments
In this case, we have luck and there is an interesting comment in there:
<!-- TODO: -->
<!-- * Remove the git directory after publishing -->That sounds indeed good. Public accessible .git/ directories are a not that uncommon low-hanging-fruit in bug bounties.
Git
First, you should learn what git is and what it is used for. From the offical page:
Git is a free and open source distributed version control system designed to handle everything from small to very large projects with speed and efficiency.
Git is a commonly used version control system for software projects of all kind. It keeps track of your source files and changes that are made to them. If you never used git, you should start by playing around with it, learn some basic commands like git add, git commit and understand how it works.
Public accessible git repositories are very sweet because they very likely contain sensitive information because people often commit security-related keys, passwords and other stuff to it. So our goal is to get this information.
If you now played a bit with git or already familiar with it, you know that git creates a hidden .git folder in your project, where you run git init. In this folder, git keeps track of all the changes and commits you make.
So let's try to access the .git/ folder from the browser, to see if it's really there.
But, we get a Forbidden message if we try to access it.
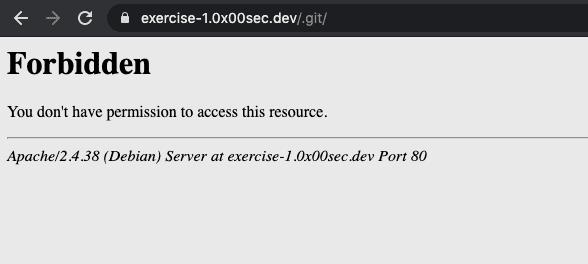
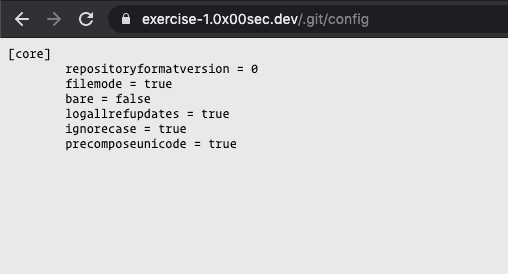
But this is only for the directory listing. If we try to access a specific file, like config we have access.
Grab the repository
Now there are several ways to get the repository. One easy way is to use wget and recursively download the repository.
wget -r --no-parent --connect-timeout=5 http://public-git.com/.git/However, in our case, this will not work, due to the Access Forbidden error code on the .git/ index. If you want to learn more about public git folders and how to download them checkout this article.
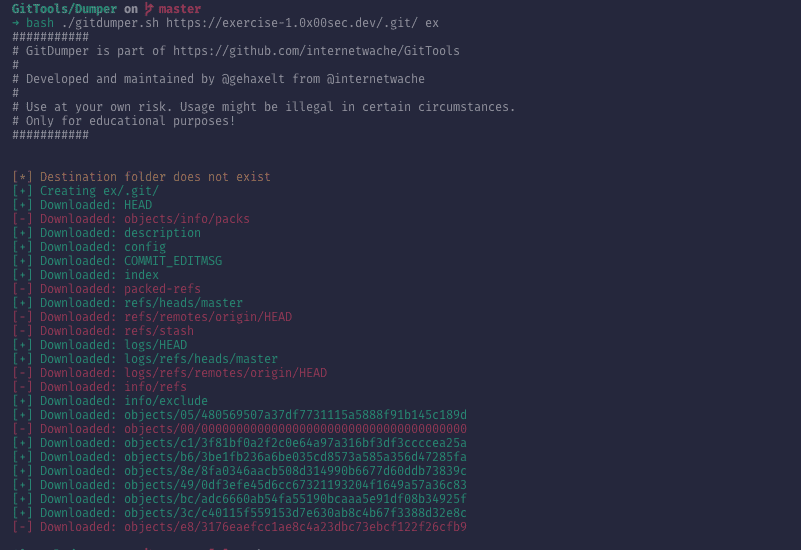
Another way is to use tools like GitTools.
With bash ./gitdumper.sh https://exercise-1.0x00sec.dev/.git/ output
I downloaded the git repository.
Now we can use the terminal git or any gui git client to check out the commits and the source.
With git status we see that there are two staged files to be deleted start.sh and index.php.
The first one is a start script for docker and the latter one the PHP source code of the page.
The login
Let's now take a deeper look into the login action in the PHP source code.
The login action looks like this:
if (isset($_POST["username"]) && isset($_POST["password"])) {
if ($_POST["username"] == "admin" && hash('sha256', $_POST["password"]) == "e83176eaefcc1ae8c4a23dbc73ebcf122f26cfb9ba5c7cf4763e96c1c38a6c6c") {
echo '<h4> '.xor_this(base64_decode("Cl9SEwgSQRVFUA1dAl1dVFkaQF0CWAQUTQ=="), $_POST["password"]).' </h4>';
} else {
echo '<h4 class="error"> Incorrect Password :) </h4>';
}
}So if our username is admin and our password matched the sha256 hash, a base64 string will be passed into xor_this(string, key).
As sha246 is not secure we can easily crack it. Or even better, try to look it up. Maybe someone already cracked it.
So I pasted the hash into CrackStation.net and the hash was already cracked and I got the password.
After the login, the flag was printed out.
Conclusion
This CTF exercise was quite fun and also quite a real-world scenario. Because public git directories are real and sadly more common then you might think.
